Understanding Zero Trust

The Zero Trust Network, or Zero Trust Architecture, model was created in 2010 by John Kindervag, who at the time was a principal analyst at Forrester. He defined it as a security concept centered on the belief that an organization should not automatically trust anything inside or outside its perimeters and instead verify anything and everything trying to connect to its systems before granting access.
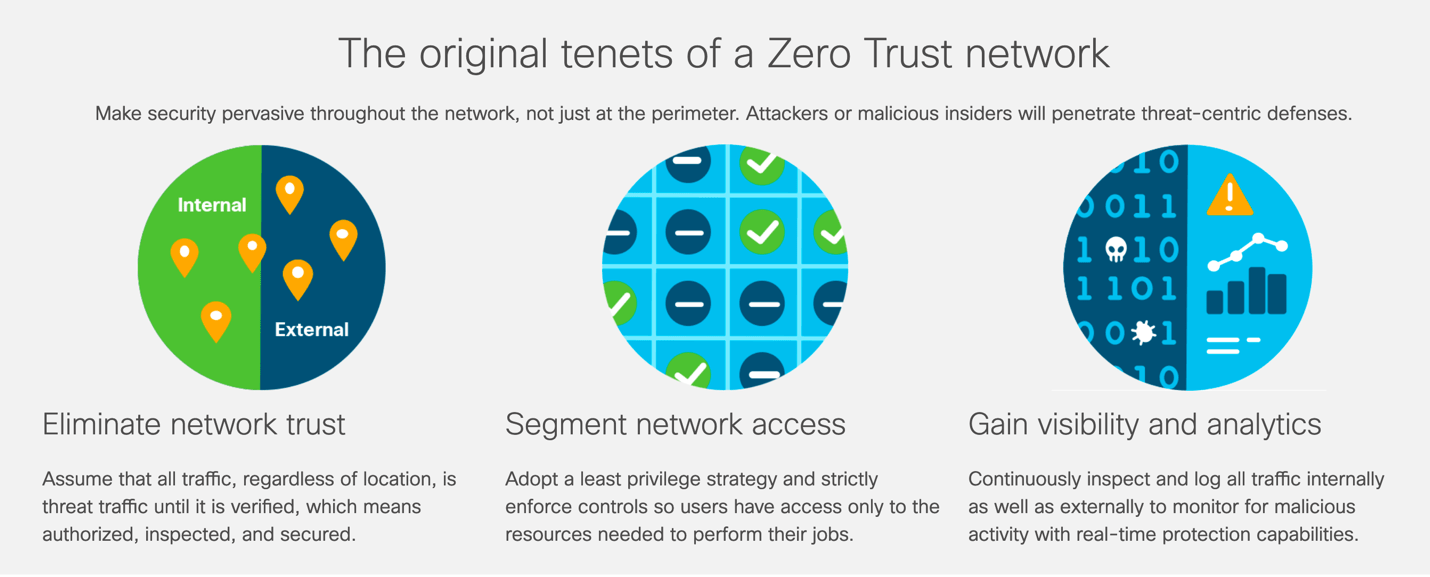
Cisco lays out the original tenants of a Zero Trust network as follows…
At the core, even though Zero Trust has been defined by many in different ways, the message is always same – only allow “just in time access” to resources on premise or in the cloud in your organization, and treat all applications and resources as internet-facing. But this concept can send many an IT pro into a spiral. What about critical infrastructure? What about VPNs? How do you do this? Why is this better?
Why all the Zero Trust fuss?
Let’s take a step back and look at why Zero Trust is getting so much traction in the first place. This comes down to a few things – the growth and severity of security incidents in recent years, and how organizations are trying to stop and defend against those threats. The defending teams in organizations (aka “blue teams”) have been losing this threat war for a while now. It seems that breaches happen more and more, and the adage is not if but when.
So, why the increase in breaches? Security budgets are increasing. More professionals are being trained. More security products are available. So, it only stands to reason that blue teams should be seeing a decline in breaches, but we are not.
Possible reasons for the increase abound. Some see the security frameworks we use as the issue. Others blame the changes in access to IT resources since COVID. Now organizations have employees and customers access data, applications and infrastructure in both cloud and on-premises scenarios, accessing that data from anywhere. Our older security models made it harder to gain access to those things and maybe allowed too much access for too long, and our digital identities were not sufficiently protected.
This brings us back to Zero Trust. This new access need with data being in the cloud, via SaaS and on premise dictated a new security model to meet these new requirements. In future blogs, I will break down this Zero Trust more in-depth, helping you navigate the pros and cons of a Zero Trust approach in your organization. Stay tuned!
Additional Resources: